the chosen plaintext attack on a high level allows the attacker oracle access to the encryption procedure.
to formalize it as a security game:
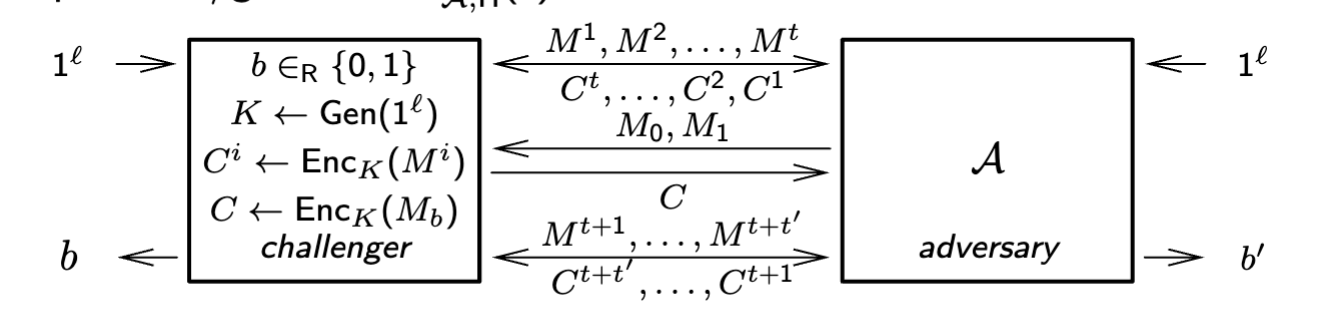
- the challenger generates a random bit and a key .
- the adversary A gets oracle access to , so they send and get ciphertexts
- the adversary then outputs (chooses) any two messages .
- the challenger picks which one to encrypt based on : and returns to A.
- the adversary can continue to request encryptions, and then must output a prediction . the adversary succeeds if .
we denote this game as
we say that a given private-key encryption scheme is CPA-secure if for all probabilistic, polynomial-time adversaries , there exists a negligible function such that
in diagram form: